TCP RESET Flag
Discover what the TCP RST flag is and its critical role in terminating TCP connections. Explore key scenarios and real-world examples that illustrate its impact on network communication and error handling in TCP.
TCP/IP
12/4/20243 min read

2. Half Open Connections:
When one side of a TCP connection sends data after the other side has already closed the connection, the receiving side may send an RST to indicate that the connection is no longer valid.
Example: A client thinks the connection is still open and sends data to the server. However, the server has already closed its end of the connection. The server will respond with an RST to indicate that the connection no longer exists.
3. Unrecoverable Errors:
When a system detects an unrecoverable condition (such as corrupted data or malfunctioning resources) while processing a TCP packet, it may reset the connection using an RST flag.
Example: A firewall may send an RST flag if it detects malicious traffic, resetting the connection to prevent further communication.
4. Abnormal Termination of a Connection:
Sometimes, an application may need to terminate a connection without waiting for the full TCP three-way termination process (FIN/ACK). In such cases, the application sends a packet with the RST flag.
Example: If a web browser crashes while a TCP session is active, the operating system might send an RST to the server to close the connection immediately.
What Happens When RST is Received?
Upon receiving a TCP packet with the RST flag:
The connection is immediately closed.
Any data in transit is discarded, and no more packets can be exchanged over that connection.
Both parties (sender and receiver) will stop communicating, and any data that wasn't acknowledged by the receiving side will be lost.
The RST flag does not require an acknowledgment, meaning the party sending the RST does not expect a response from the recipient.
When is RST Used Intentionally?
Network Middleboxes (Firewalls, Load Balancers): They might send RST packets to drop connections perceived as suspicious or unwanted. For example, firewalls can use RST packets to reject connections without letting the application layer know.
Application Design: Applications may use RST to abort connections when they encounter errors, or when they need to reset the state without going through the regular FIN handshake.
Proactive Reset of Faulty Connections: If an application detects that it is in an unexpected state (e.g., resources unavailable or miscommunication), it can send an RST to forcefully terminate the connection and start over
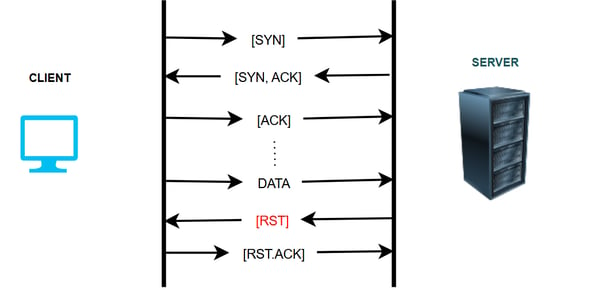
Example of a RST Scenario
Client Connection to a Closed Port
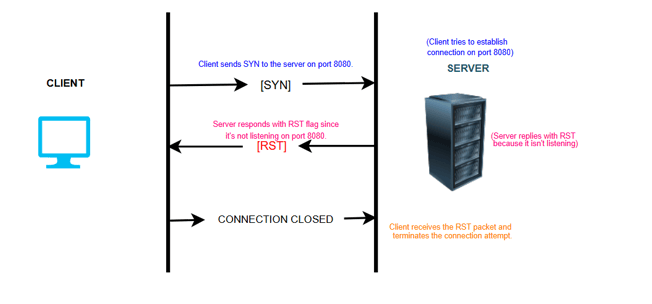
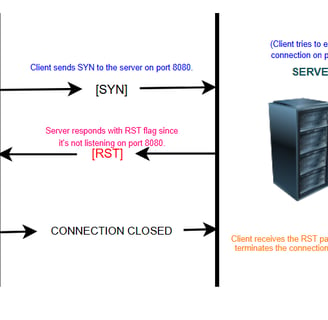
Imagine a client trying to connect to a server on port 8080, but the server is not listening on that port:
1. Step 1: The client sends a TCP SYN packet to the server on port 8080, attempting to establish a connection.
2. Step 2: Since the server is not listening on port 8080, it responds with a TCP segment that has the RST flag set.
3. Step 3: The client receives the RST packet and knows that the connection cannot be established. The client will terminate its connection attempt immediately without retrying further.
In this case, the RST flag effectively prevents the client from waiting indefinitely for a response and signals that the port is not accepting connections
Key Points About RST:
It is used to abort connections.
It helps clean up invalid, broken, or suspicious connections.
It’s a signal of error conditions or miscommunication.
It is often sent by devices like firewalls or middleboxes to drop unwanted connections.
Let me know if you need more details on any of these scenarios!
The RST (Reset) flag in TCP is used to abruptly terminate a connection or signal an error condition. It indicates that the connection should be reset immediately without completing the normal shutdown procedure. The RST flag is set when there is some kind of problem with the TCP connection.
Scenarios Where RST Flag is Sent
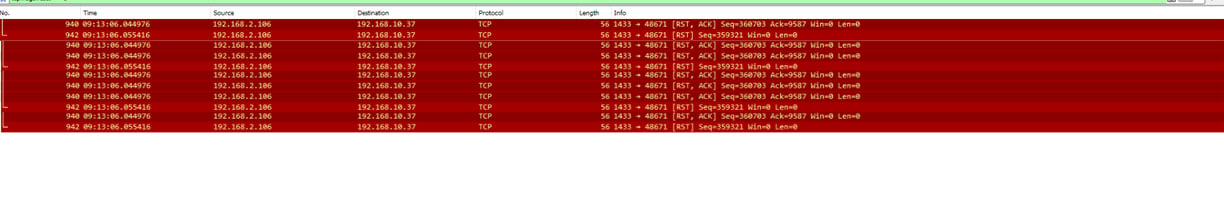
1. Connection to a Non Listening Port:
If a client tries to send a packet to a closed port on the server, the server responds with an RST flag, indicating that it is not accepting connections on that port.
Example: A client attempts to connect to a server on port 8080, but the server is not listening on that port. The server will respond with a TCP segment containing the RST flag.
cybrescue@gmail.com
Ping us incase of any.....
Connect with us at
support@cybrescue.com
